Last updated: January 25, 2023
TERMS AND CONDITIONS
The website Spoutible.com along with any other URL, mobile application or similar technology that redirects to or facilitates access to the website (together, "Spoutible", “we”, “us” or “the Platform”) is owned and operated by Spoutible Inc., a corporation duly incorporated in and existing under the laws of the State of Delaware and Registered Office at 442 5th Avenue #2107, New York, NY 10018.
PLEASE READ THIS DOCUMENT CAREFULLY BEFORE USING THE SPOUTIBLE PLATFORM. BY USING, ACCESSING, UPLOADING OR DOWNLOADING ANY INFORMATION TO OR FROM THE PLATFORM, YOU CONFIRM THAT YOU ARE OF AT LEAST 13 YEARS OF AGE AND AGREE TO BE BOUND BY OUR TERMS AND CONDITIONS SET FORTH BELOW. IF YOU DO NOT WISH TO BE BOUND BY THESE TERMS, YOU ARE ADVISED NOT TO CONTINUE USING THE PLATFORM ANY LONGER.
- REGISTRATION OF USER ACCOUNT
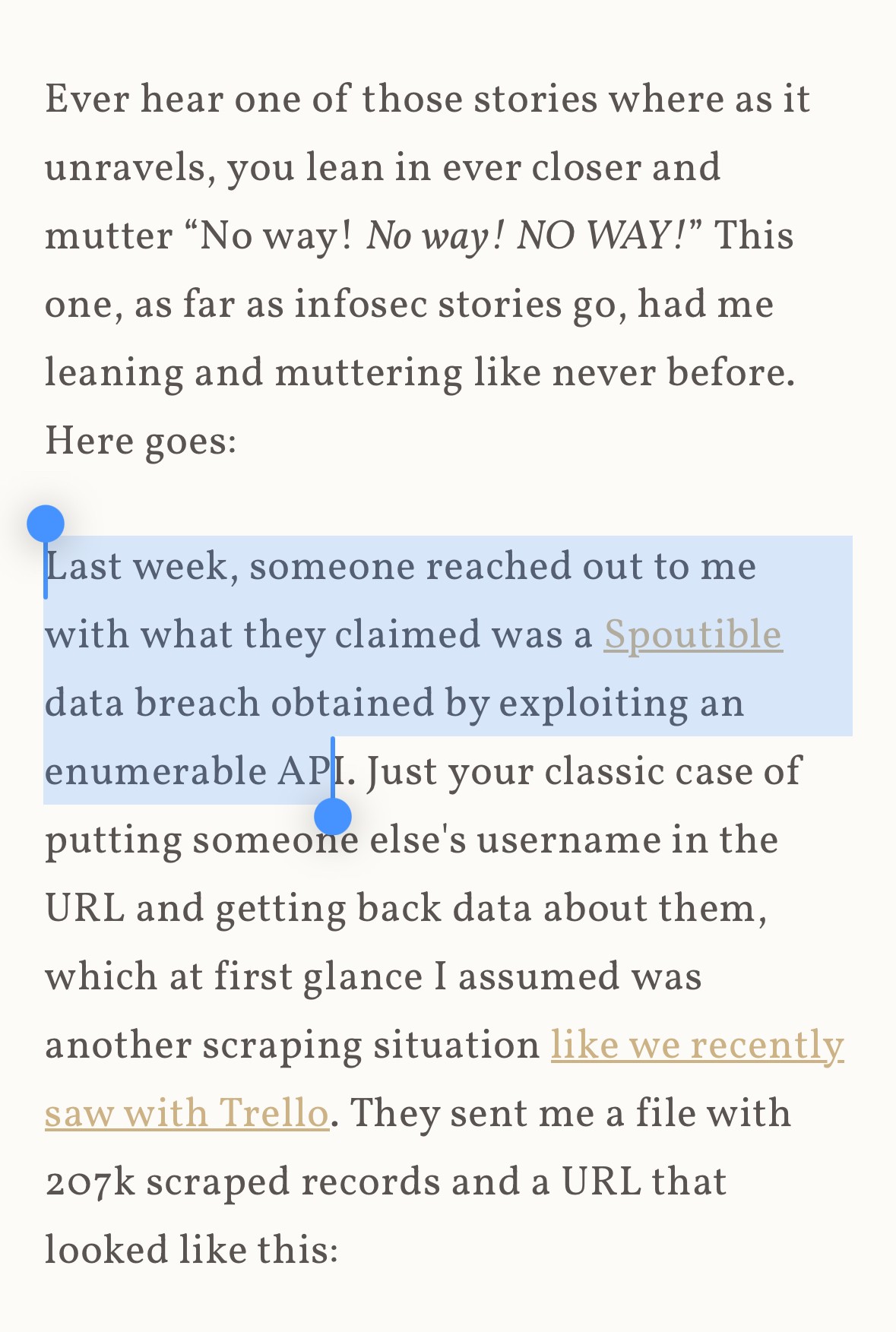
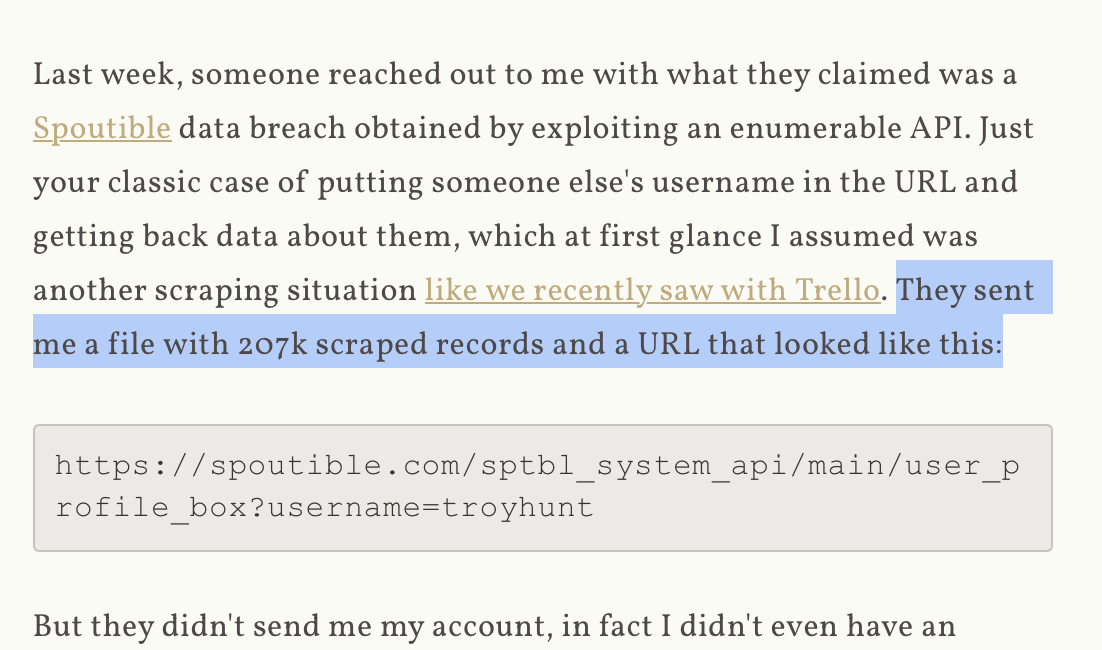
Spoutible is a free microblogging and social media platform, where users can post, share, discover, discuss and directly message various types of textual and graphical content (“Content”) across the world. In order to successfully use Spoutible, you must be at least 13 years of age and must complete the registration process by submitting your first name, last name, email address, gender, date of birth, and telephone number. You must not use any other person's account to access Spoutible. You must not allow any other person to use your account to access Spoutible. You are responsible for maintaining the confidentiality of your account login information and are fully responsible for all activities that occur under your Account. You agree to notify us immediately of any unauthorised use, or suspected unauthorised use of your account or any other breach of security. Under no circumstances shall Spoutible have any liability to you for any loss or damage of any kind incurred as a result of the use (or inability to use) of the Platform or reliance on any content and information provided on the Platform. Your use of the Platform and your reliance on any content therein is solely and completely at your own risk.
- CONTENT DISCLAIMER
Spoutible allows all registered users to post, share, publish and otherwise upload and make available various types of Content in or through the Platform. You are solely responsible for such Content and hereby ensure that it does not offend any third-party rights, including but not limited to any applicable intellectual property rights, privacy rights, publicity rights, contractual rights and does not in any way be considered against applicable laws. We make no representation as to the completeness or accuracy of any Content in the Platform and nothing herein shall be considered as a referral, endorsement, recommendation, verification, warranty or guarantee with respect to the validity, accuracy, availability, completeness, safety, legality, quality or applicability of any Content on the Platform. Spoutible reserves the right, but is not obligated to, delete, modify, edit or update any Content that we, in our sole discretion, deem to be in violation of these Terms and Conditions or deem to be otherwise unacceptable. Notwithstanding the above, by accepting these Terms and Conditions you grant us the right and license to use, modify, display and distribute such Content by and through the Spoutible Platform and make it available to others, who may also use such Content subject to these Terms and Conditions.
- ACCEPTABLE USE OF THE PLATFORM
In order to maximize your user experience in using the Spoutible Platform, and avoid, eliminate or minimize disruptive activities, we kindly ask you to maintain the following:
- do not use the Platform in any way or take any action that may undermine, disrupt, damage or manipulate its working functionality, performance, availability or accessibility;
- do not copy, decompile, reverse engineer, disassemble, attempt to derive the source code of, modify or create derivative works of the Platform, or any updates or any part thereof;
- do not use the Platform in any manner that is unlawful, illegal, fraudulent or harmful, or in connection with any unlawful, illegal, fraudulent or harmful purpose or activity;
- do not impersonate any person or entity, misrepresent any affiliation with another person, entity, or association, use false IP addresses or headers, or otherwise conceal your identity for any purpose;
- do not publish any personal or confidential information belonging to any person or entity without obtaining consent from such person or entity;
- do not violate, plagiarize, or infringe on the rights of third parties, including without limitation copyright, trademark, trade secret, privacy, publicity or other proprietary rights;
- do not use any data collected from the Platform for any direct marketing activity (including without limitation direct messaging, email marketing, SMS marketing, telemarketing and direct mailing).
- Abide by our Community Policies available at https://www.spoutible.com/Policies
- SUSPENSION OF SERVICE
Spoutible reserves the right to fully or partially suspend, discontinue, or cease providing, at any time and from time to time, temporarily or permanently, any of the Services with or without notice, and shall have no liability or responsibility to you in any manner whatsoever if it chooses to do so. All provisions of these Terms and Conditions which by their nature should survive such suspension or termination shall survive, including, without limitation, intellectual property ownership, warranty disclaimers, indemnity and limitations of liability.
- THIRD PARTY LINKS AND ADVERTISEMENTS
Spoutible may provide external links and advertisements submitted by or directed towards third party websites and services. Unless expressly stated otherwise, such advertisements do not signify that Spoutible endorses and/or is associated with such third-party websites and services in any manner including, but not limited to, the content, accuracy, quality, nature, appropriateness, decency, functionality, performance, reliability, completeness, timeliness, validity, safety, legality or any other aspect thereof. We accept no responsibility for third party advertisements contained within Spoutible. If you agree to purchase goods and/or services from any third party who advertises in this Platform, you do so at your own risk and these Terms and Conditions remain no longer applicable for such third party goods or services.
- DISCLAIMER OF WARRANTIES
By using the Spoutible Platform, you hereby acknowledge and agree that such usage is at your sole risk and responsibility. To the maximum extent permitted by applicable law, Spoutible is provided on an “as is” and “as available” basis without warranties of any kind, either expressed or implied, including, but not limited to, all warranties of quality, accuracy, completeness, reliability, conditions of merchantability, fitness for a particular purpose, title or non-infringement. We do not warrant that the products and services offered through Spoutible will meet your specific requirements, that the Platform will be uninterrupted or error-free or free from viruses or similar harmful matter or that any defects in Platform will be immediately corrected. No oral or written communication offered by Spoutible will create any warranty for this purpose.
- LIMITATION OF LIABILITY
Under no circumstances will Spoutible and any of its directors, shareholders, employees and agents be liable for any incidental, consequential, or indirect damages including, but not limited to, business interruption, damages for loss of profit, loss of data, loss of goodwill and the like arising out of the use or inability of use of the service/ information provided on or downloaded from the Platform, or any delay in the processing of such information or services. For removal of doubt, this includes situations where there is any failure or delay in performance of any of the obligations under these Terms and Conditions that is caused by events outside our reasonable control (force majeure events). Notwithstanding the above, nothing under these Terms and Conditions will limit or exclude any liabilities that may not be excluded under applicable law.
- INDEMNIFICATION
You agree to indemnify, defend and hold harmless Spoutible, its officers, directors, employees, agents, consultants, representatives and agents from and against all losses, damages, suits, judgments, costs and expenses (including litigation costs and reasonable attorneys' fees) arising out of or in connection with (a) your use of or inability to use Spoutible (b) your violation of any provision of these Terms and Conditions or your violation of any rights of a third party, or (c) your violation of any applicable laws, rules or regulations. Spoutible reserves the right, at its own cost, to assume the exclusive defense and control of any matter otherwise subject to indemnification by you, in which event you will offer complete cooperation with Spoutible in asserting any available defenses.
- INTELLECTUAL PROPERTY
All information and content displayed in the Platform including text, graphics, designs, photographs, videos, typefaces, look and feel, format, and the like is owned and/or licensed by Spoutible unless expressly specified otherwise, and are protected by international laws on patents, copyrights, trade secrets, trade names, trademarks (whether registered or unregistered), domain names and other applicable rights. Notwithstanding the above, Spoutible hereby disclaims any and all rights and claims to the copyright or any other right over any third-party content featured in the Platform unless expressly specified otherwise. By agreeing to these Terms and Conditions you understand and agree to not modify, copy, reproduce, republish, upload, post, transmit, or distribute, in any manner, any material on or from Spoutible, including text, graphics, logos and designs for any purpose whatsoever or allow any third party to do so.
- COPYRIGHT PROTECTION
If you believe there has been any unauthorized uploading or sharing of your intellectual property by or through our Platform amounting to copyright infringement, please get in touch with us immediately in accordance with the procedure set forth below. We value the intellectual property rights of all copyright holders and will process and investigate notices of alleged infringement and promise to take appropriate actions under applicable intellectual property laws with respect to any alleged or actual infringement.
For us to process your complaint as a Notice pursuant to the United States Digital Millennium Copyright Act 17 U.S.C. §512(c), a notification of the claimed copyright infringement should be emailed to Spoutible’s Copyright Agent at: [email protected] with the subject line “DMCA Takedown Request” and containing the following information:
- a description of the copyrighted work or other intellectual property that you claim has been infringed;
- an electronic or physical signature of the person authorized to act on behalf of the owner of the copyright or other intellectual property interest;
- a detailed description of where the material that you claim is infringing is located on the Website, so as to assist us with prompt identification;
- your postal address, telephone number, and email address;
- a statement by you that you have a good faith belief that the disputed use is not authorized by the copyright or intellectual property owner, its agent, or the law;
- a statement by you, made under penalty of perjury, that the above information in your Notice is accurate and that you are the copyright or intellectual property owner or authorized to act on the copyright or intellectual property owner’s behalf.
- ELECTRONIC COMMUNICATIONS
The communications between you and Spoutible use electronic means. For contractual purposes, you (a) consent to receive communications from Spoutible in an electronic form; and (b) agree that all terms and conditions, agreements, notices, disclosures, and other communications that Spoutible provides to you electronically satisfy any legal requirement that such communications would satisfy if it were to be in a hardcopy writing. With your informed consent (opt-in), such electronic communication may also include periodic emails and/or other messages for our internal marketing and promotional purposes. We take all reasonable measures to ensure that our marketing communications are compliant with the applicable laws.
- GENERAL INFORMATION
These Terms and Conditions shall be governed by and construed in accordance with the laws of the State of New York without regard to principles of conflict of laws, and all disputes as to the validity, execution, performance, interpretation or termination of these Terms will be submitted to the exclusive jurisdiction of the competent courts thereof. If any provision of these Terms and Conditions is found by a court of competent jurisdiction to be invalid, such invalidity will not affect the enforceability of any other part or provision of this Agreement.
Spoutible reserves the right, at their sole discretion, to modify these Terms and Conditions at any time, and such modifications shall be effective immediately upon posting of the same on the Platform. You agree to review this document periodically to be aware of such modifications and your continued access or use of the Spoutible Platform shall be deemed as a conclusive acceptance of such modified Terms and Conditions.
If you have any further questions, comments or requests regarding these Terms and Conditions, please contact us at [email protected].
![]() Isa-Lee Wolf @IsaLeeWolfSo I was on the bad site for a second, and found this.10:41 AM - Feb 06, 2024
Isa-Lee Wolf @IsaLeeWolfSo I was on the bad site for a second, and found this.10:41 AM - Feb 06, 2024